
BLOG
Caught in a Spider’s Web | A Fly-By View of Healthcare Data Security Vulnerabilities
Published On September 5, 2019
Blog Post by Brian Selfridge, Partner and Carol Kleywegt, Contributing Writer at Meditology Services
Just as a spider spins a web to catch unsuspecting insects, cybercriminals spin clever traps to capture patient data from healthcare organizations. Healthcare security executives must work on evolving their data security programs to avoid being caught in a dangerous web that can threaten patient health, security and privacy.
As recently as June 2019, one of the largest healthcare breaches involving hackers to date (25 million patient records) was identified on the American Medical Collections Agency (AMCA) database of healthcare client records. Like a spider’s web casts a wide-net, these hackers accessed patient records from a variety of clinical lab testing providers including LabCorp, Quest Diagnostics and BioReference Laboratories.
To combat these savvy data thieves, healthcare entities and their vendor communities must develop a better understanding of how to protect patient information as it becomes disseminated to an unprecedented number of locations and formats.
Understanding Threat Actors
To catch a thief, you must understand their species, classification and behaviors. The most common threat actors associated with compromising the confidentiality, integrity, or availability of healthcare resources include:
- Financially-motivated malicious outsiders (e.g. organized crime)
- Nation States (malicious outsiders)
- Hacktivists (malicious outsiders)
- Terminated workforce members
- Insiders: non-malicious & malicious
- Environmental factors
Mature data security programs must include security controls to address exposure to these varied threat actors.
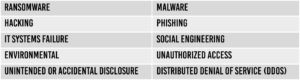
Tactics Used to Steal Data
Predators are becoming increasingly creative in luring your workforce into traps to reveal sensitive information. Specific tactics enable an individual to gain access to information systems with an intent to disrupt operations or obtain protected information. These methods (also known as threat vectors) could directly result in the loss of the confidentiality, availability, or integrity of the data belonging to healthcare entities.
Some of the most common threat vectors within healthcare environments include:
Evolving Defense Mechanism
Evolve your organization’s defense mechanism by educating your workforce on these camouflaged risks lurking in the healthcare environment. Recent healthcare breach incidents reveal that internal workforce training and business associate security practices must be strengthened. For example, in a 2019 HIMSS study, email phishing (among internal workers) was the initial point of data compromise for 69 percent of breaches at hospitals.[1] Educate, train and plan for exposure to these data predators and their tactics.
Maturing Your Security Program
Growing, strengthening and expanding your information security program can keep patient information safe from the tangled webs of data predators. Here are five tips for strengthening healthcare information security programs to address emerging threats to the business:
- Maintain a risk register that aligns with OCR’s expectations and considers emerging threats and threat actors.
- Make sure your risk management plan addresses infrastructure shifts including cloud hosting and IoT.
- Establish and mature a data governance security program and model that enhances visibility and protections for data as it moves throughout its lifecycle.
- Focus on third party risk management as a primary pillar for the risk management program for 2020 and beyond.
- Leverage automation and third-party services to cover critical controls that cannot be adequately addressed with limited internal resources.
By following these tips, your organization can evolve into a more secure entity designed to protect against current and emerging threats in the healthcare ecosystem.
Read more about methods to evolve your organization’s security posture in our white paper: 2019 | The Year of Metamorphosis for Healthcare Data Security.