BLOG
CISA Publishes Cyber Performance Goals for Healthcare
Published On November 8, 2022
The Cybersecurity and Infrastructure Security Agency (CISA) has been hinting for weeks about a pending announcement on cybersecurity for the nation’s critical infrastructure including healthcare. That update has arrived in the form of a major publication titled CPG: Cross-Sector Cybersecurity Performance Goals.[1]
The CPGs provide a mechanism for healthcare organizations and other critical sector entities to prioritize their implementation of the most effective and essential security controls required to defend against emerging cyberattacks.
This blog provides an overview of the CPGs including the history and genesis, definition and components, and practical applications for the CPGs for healthcare organizations.
History and Context
President Biden issued several executive orders and national security memos in 2021 including Improving the Nation’s Cybersecurity and Improving Cybersecurity for Critical Infrastructure Control Systems.
The national security memo was issued following the high-profile cyberattack against Colonial Pipeline that resulted in the declaration of a national security emergency. The memo required the CISA, in coordination with the National Institute of Standards and Technology (NIST) and the interagency community, to develop baseline cybersecurity performance goals, or CPGs, that are consistent across all critical infrastructure sectors.
The following resources published by Meditology Services and CORL Technologies provide more information about these presidential executive orders.
- Podcast: CyberPHIx Special Episode: Presidential Executive Order for Improving the Nation’s Cybersecurity
- Podcast: CyberPHIx Roundup: Industry News and Trends August 2021
- Blog: Regs on the Radar: Emerging Supply Chain Regulations & Standards
What are the Cyber Performance Goals (CPGs)?
According to the CISA[2], the CPGs are “a prioritized subset of IT and operational technology (OT) cybersecurity practices that critical infrastructure owners and operators can implement to meaningfully reduce the likelihood and impact of known risks and adversary techniques. The goals were informed by existing cybersecurity frameworks and guidance, as well as the real-world threats and adversary tactics, techniques, and procedures (TTPs) observed by CISA and its government and industry partners. By implementing these goals, owners and operators will not only reduce risks to critical infrastructure operations, but also to the American people.”
The CPGs are intended to be:
- A baseline set of cybersecurity practices broadly applicable across critical infrastructure with known risk-reduction value
- A benchmark for critical infrastructure operators to measure and improve their cybersecurity maturity
- A combination of recommended practices for IT and OT owners, including a prioritized set of security practices
- Unique from other control frameworks as they consider not only the practices that address risk to individual entities, but also the aggregate risk to the nation
The CISA comments up front that the CPGs are voluntary in nature. President Biden’s memo did not compel organizations to adopt the CPGs or provide reporting on them to any government agency. It would not be surprising if the CPGs were leveraged as part of future cybersecurity laws, but for now, they are voluntary.
The CISA acknowledges that the CPGs are not comprehensive in nature and are not designed to replace security control frameworks like NIST Cybersecurity Framework (NIST CSF). Rather, the CPGs are intended to provide a starting point for organizations to implement the most critical security controls first and to help prioritize remediation for areas that will have the greatest impact on thwarting the latest attack methods. The CPGs are mapped and aligned to the NIST CSF and are framed by the CISA as “a kind of QuickStart guide” for the NIST CSF.
CPG Security Domains
The CPGs are organized into 8 categories or domains:
- Account Security
- Device Security
- Data Security
- Governance and Training
- Vulnerability Management
- Supply Chain / Third Party
- Response and Recovery
- Other (e.g. Network Segmentation, Email Security)
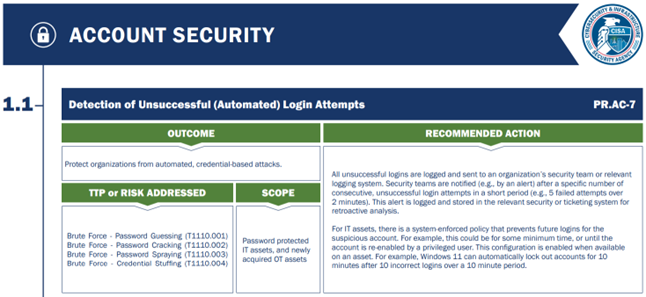
An example of one of the Account Security CPGs is provided below to give a sense of the structure and format of the publication.
Figure 1 – Example CPG for Detection of Unsuccessful (Automated) Login Attempts[3]
CPG Structure & Design Considerations
The CISA explained its selection criteria for how it chose the CPGs as follows:
- Significantly and directly reduce the risk or impact caused by commonly observed, cross-sector threats and adversary TTPs
- Clear, actionable, and easily definable
- Reasonably straightforward and not cost-prohibitive for even small- and medium-sized entities to successfully implement
Each CPG follows the same basic model that includes 5 data elements:
- The security outcome the CPG will enable
- The TTP or risk addressed by the CGP (including mapping to MITRE ATT&CK TTPs)
- The scope of the security practice – this mostly refers to IT or OT or both, but there are some more specific examples like windows-based IT assets or departing employees
- Recommended actions which are practical tips and examples of how an organization can implement the CPGs
- The NIST CSF subcategory references that relate most closely to the security practice
The CPG publication provides handy and practical materials to try to solve the “where do I begin problem” that so many healthcare organizations face when looking to adopt security frameworks. There is a downloadable Excel version of the CPGs that lists all CPGs and maps them back to other frameworks.
The publication also contains a worksheet with some components that would come in handy for a low-maturity organization. This worksheet contains tables that include all the data elements outlined above, but it also includes:
- High, medium, and low-impact ratings for the controls
- High, medium, and low complexity rating in terms of implementation level of effort
- Specific verbiage on recommended actions relative to the scope of the control (including specific advice for OT vs IT implementations)
- An assessment checklist for current state and 1-year-later state to allow organizations to get started implementing a control while leaving room to mature over time
What’s Next for CPGs?
Meditology recommends that healthcare organizations of all shapes and sizes review the CPGs and leverage them to support and mature their cybersecurity programs.
For smaller organizations, the CPGs provide an excellent “on-ramp” to the adoption of larger, more complex security control frameworks like the NIST CSF or HITRUST. The CPGs provide the greatest “bang for the buck” in terms of cost-effective security controls that can greatly limit the likelihood and impact of cyberattacks.
For larger organizations, the CPGs are an excellent resource to prioritize ongoing assessment and remediation activities. The areas outlined in the CPGs should be prioritized above other assessment results to shore up security controls related to the latest threats and attack vectors facing the industry.
The CPG publication is one example of a series of high-quality publications that the CISA and other federal agencies have produced in recent months.
Contact our team here at Meditology to learn more about the CPGs and how your organization can adopt and implement these controls to safeguard the organization and critical infrastructure systems.
[1] https://www.cisa.gov/sites/default/files/publications/2022_00092_CISA_CPG_Report_508c.pdf
[2] https://www.cisa.gov/sites/default/files/publications/2022_00092_CISA_CPG_Report_508c.pdf
[3] https://www.cisa.gov/sites/default/files/publications/2022_00092_CISA_CPG_Report_508c.pdf