
BLOG
NIST SP 800-53 Rev 5: Sizing Up the New Security Standard in Town
Published On October 8, 2020
Blog Post by Maliha Charania, ITRM Manager at Meditology Services
The National Institute of Standards and Technology (NIST) has announced an updated version of their flagship security controls framework NIST Special Publication (SP) 800-53. The new version, Revision 5 or “Rev 5”, update is the first overhaul of the NIST SP 800-53 framework in over seven years and represents critical updates that reflect the modern cyber threat landscape.
This blog post will help provide some insight into the new controls framework version, its differences from prior iterations and other related standards, and its applicability for healthcare organizations.
NIST SP 800-53: The Granddaddy of Security Controls Frameworks
NIST SP 800-53 has historically served as the foundation of US government security controls and has found widespread adoption in healthcare and other critical infrastructure and private sector organizations. NIST SP 800-53 Rev 4 was released in April 2013 and was followed up by the creation of the NIST Cybersecurity Framework (CsF) in February of 2014. The NIST CsF was designed to be a more “approachable” security framework that employed more business-friendly language and structure to support adoption both inside and outside of federal entities. As one might expect, NIST has designed the new SP 800-53 Rev 5 controls to integrate and align with the NIST CsF framework. While NIST CsF rapidly gained adoption in healthcare, NIST SP 800-53 remains in use for many healthcare organizations that prefer a more rigorous security controls set.
Another prominent security controls framework for healthcare organizations is the HITRUST Common Security Framework (HITRUST CSF). The HITRUST Alliance released the HITRUST CSF in 2007 and relied heavily upon NIST SP 800-53 and ISO controls as the foundation of the framework. Note: Meditology’s founding partner Cliff Baker served as the chief architect of the HITRUST CSF and designed the model that remains in use today to normalize security controls for healthcare entities including NIST SP 800-53, ISO, HIPAA, NIST CsF, state and global regulations, and more.
What’s New: Comparing Rev 4 to Rev 5
According to NIST, Rev 5 is not just a minor update but is a “complete renovation”[1] of the standard. Rev 5 adds more than 45 new base controls, 150 new control extensions, and approximately 100 new parameters to existing controls.
The most significant updates include the addition of controls around third-party risk and supply chain, privacy, and new “state of the practice” areas like cyber resiliency, secure systems design, and governance models. The framework updates have also been designed to scale and apply to a variety of systems and applications from largescale IT and cloud infrastructures down to individual mobile and IoT devices.
Here is a quick view of the control family changes from Rev 4 to Rev 5.
NIST SP 800-53 Rev 4 Control Families
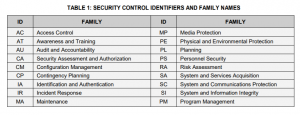
NIST SP 800-53 Rev 5 Control Families
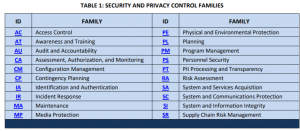
NIST lists the following areas as the most significant changes to the standard. [2] I have included commentary for each are as to how these changes may impact healthcare entities.
- Integrating supply chain risk management: Rev 5 establishes a new Supply Chain Risk Management (SCRM) control family and integrates supply chain risk management aspects throughout the other control families to help protect system components, products, and services that are part of critical systems and infrastructures. The SCRM controls help ensure that security and privacy requirements, threats, and other concerns are addressed throughout the system development life cycle and the national and international supply chains.
Third-party and vendor risk management has become a dominant theme for security programs for healthcare organizations in 2020. The volume of third-party application and systems deployed in healthcare is rising daily, with typical organizations leveraging hundreds to thousands of vendors to support critical clinical and business functions. The breach trends for these same third-party entities are causing healthcare organizations to ramp up investment in vendor risk management programs, teams, and processes.
The addition of supply chain risk management controls to the NIST SP 800-53 catalog is a much needed and long overdue adjustment to reflect the industry’s dependence on third-party vendors.
- Making controls outcome-based: Rev 5 accomplishes this by removing the entity responsible for satisfying the control (i.e., information system, organization) from the control statement—thus focusing on the protection outcome to be achieved by the application of the control. Note that for historical continuity, Appendix C, Control Summaries now includes an “implemented by [system/organization]” column.
The movement to outcomes-based controls represents a fundamental mindset shift that will help healthcare organizations to move away from a focus on tactical “busy work” and towards strategic outcomes that can measurably reduce risk.
At Meditology, this line of outcomes-based thinking has been at the core of our healthcare enterprise risk management and reporting services. Learn more about our recommendations in our related blog post, Enterprise Risk Reporting: The Healthcare CISO’s Achilles Heel.
- Consolidating the control catalog: Information security and privacy controls are now integrated into a seamless, consolidated control catalog for systems and organizations. The privacy controls in Appendix J of Revision 4 have been incorporated into a new privacy family and the existing Program Management family. Some of the privacy controls were also incorporated into current security controls—allowing the controls to serve both the security and privacy communities as well as achieving more efficient control implementation.
Let’s face it, there is an overwhelming volume of security controls to consider when adopting standards like NIST and HITRUST. Adding privacy controls into the mix is a welcome and necessary evolution, but it also contributes to the number and complexity of the overall control catalog. The consolidation of controls and logical restructuring of the framework is a necessary form of “hygiene” for any control framework that strives to keep up with complex and evolving business and threat landscapes. The HITRUST Alliance, for example, is continually reviewing, revising, and releasing new versions of the HITRUST CSF for this very reason. We suspect another major overhaul to HITRUST will be coming soon to align with NIST SP 800-53 Rev 5.
There are some drawbacks, however, to shuffling the deck with security control standards like NIST. Historic trending of compliance and maturity of the security program can become challenging to compare apples to apples over time. There is also an educational component wherein security, compliance, and business leaders need to become familiar with the new terminology, structure, and nuances of update control requirements in order to assess, communicate, and apply the new standards effectively.
- Separating the control selection process from the controls: Having a consolidated, stand-alone control catalog allows the controls to be used by different communities of interest, including systems engineers, security architects, software developers, enterprise architects, systems security and privacy engineers, and mission or business owners. These communities of interest can now better collaborate on points of intersection or use an individualized process as needed for selecting controls to manage risk consistent with their mission and business needs as well as internal organizational policies and procedures.
For healthcare entities, this change may be a helpful way to open up the dialog around security controls and standards to stakeholders and audiences outside of the security, risk, IT, and compliance teams. NIST SP 800-53 has traditionally been known to use some fairly antiquated “tech speak” that can be challenging to use when communicating with non-technical audiences.
- Transferring control baselines and tailoring guidance to a separate publication: Control baselines have been moved to the new NIST SP 800-53B, Control Baselines for Information Systems and Organizations. The three security baselines and one privacy baseline are applicable to federal agencies and reflect specific requirements under the Federal Information Security Modernization Act and the Office of Management and Budget (OMB) Circular A-130. Other organizations may choose to develop their own customized baselines in accordance with their mission or business needs and organizational risk tolerance.
In practical terms, we interpret this to mean that the guidelines and control baselines may evolve over time. Having a separate document and forum for communicating those changes and guidelines makes sense so that we don’t need to wait another seven years to have the NIST catalog update to reflect our rapidly changing businesses and threat landscape.
- Improving descriptions of content relationships: Rev 5 clarifies the relationship between requirements and controls as well as the relationship between security and privacy controls. These relationships are important to understand whether you are selecting and implementing controls at the enterprise level or as part of a life cycle-based systems engineering process.
There are significant dependencies between security and privacy functions for healthcare entities. Understanding the inter-relationship and overlap between those controls is essential to effective privacy and security risk management for the enterprise.
- Adding new state-of-the-practice controls: As cyber threats evolve rapidly, new safeguards and countermeasures are needed to protect the critical and high value assets of organizations including individual’s privacy and personally identifiable information. The new controls in Rev 5 are based on the latest threat intelligence and cyber-attack data (e.g., controls to support cyber resiliency, secure systems design, security and privacy governance, and accountability).
Agility to adapt to evolving threats will be critical for the successful deployment of the new NIST controls for healthcare entities. These latest controls provide a useful mechanism to get a handle on threats that face our organizations in the near term. These threats evolve quickly, however, so don’t wait too long to check out these updates before they have the potential to become stale.
Closing Thoughts: What’s Next?
NIST SP 800-53 Rev 5 is a welcome addition and update to the security controls catalog for healthcare organizations and overall cybersecurity industry.
For organizations that are currently using NIST SP 800-53 Rev 4 as the foundation for their programs, this update will require some near-term strategic planning and tactical updates heading into 2021 to calibrate the program to the new requirements. This includes updating policy and procedure documentation, risk analysis models, and reporting at a minimum. Given the large-scale overhaul of the controls, it will also require some substantive implementation work to rollout new and updated controls. These initiatives will need to be balanced against the organization’s overall security, privacy, and risk strategic plans and prioritized accordingly alongside other remediation efforts.
For organizations aligned with the HITRUST CSF including those that have achieved or are pursuing HITRUST certification, these changes will likely result in substantive updates to the HITRUST CSF that will be rolled out in due time via the HITRUST Alliance. It is advisable for such organizations to review the standard in detail now and start to lay the groundwork for policy, procedure, and implementation updates to avoid a fire drill when the new versions of HITRUST get released in the coming months.
Contact our team here at Meditology to learn more about the NIST SP 800-53 Rev 5 changes and to discuss implications for your organization.
RESOURCES
[1] https://www.nist.gov/blogs/cybersecurity-insights/next-generation-security-and-privacy-controls-protecting-nations
[2] https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-53r5.pdf