BLOG
OCR Presents: 2019-2020 Year in Review
Published On June 16, 2020
Blog Post by Cliff Baker, Managing Partner at Meditology Services
I recently had the opportunity to deliver a presentation alongside leadership from the Office for Civil Rights (OCR) on the state of HIPAA Security Rule compliance and enforcement. We covered a lot of ground, and I will summarize some of the key themes here to catch you up to speed.
Key takeaways from our joint session with OCR included:
- Paradigm shifts and risks for healthcare delivery via third party cloud-hosted solutions
- HIPAA & COVID-19 updates and enforcement exceptions
- HIPAA compliance and enforcement actions and trends
- Breach source and reporting trends
- Recurring HIPAA compliance issues
- Corrective actions and best practices recommendations
Paradigm Shifts and Risks for Healthcare Delivery via Third-Party Cloud-Hosted Solutions
The breach data and enforcement updates supplied by OCR reinforced my perspective on the paradigm shift currently underway for healthcare delivery in the migration of critical business functions to third party cloud-based platforms. I believe this movement has reached a critical-mass threshold and introduces game-changing implications for information security and compliance programs.
The ability to get visibility into third-party data supply chains and their respective security and compliance postures will soon become the paramount mandate for information security programs. Effective healthcare security and compliance programs of the next decade must quickly adjust their orientation in 2020 towards the oversight and protection of downstream vendors and systems responsible for critical business functions.
Electronic Boundaries are Rapidly Disappearing
Gone are the days of 1-on-1 relationships between physicians and patients for the evaluation and delivery of care. High-quality patient care in 2020 and beyond requires an army of specialists, technology, analytics, and data, the majority of which are supplied by third party organizations. These third parties, in turn, leverage their own partners and suppliers as terabytes of sensitive data gets shuffled along to a growing number of people and platforms.
The speed to adoption and implementation of third-party cloud-hosted solutions vastly surpasses legacy IT implementation models. The downside to that rapid deployment pace, however, is that security and compliance teams have less time to evaluate and remedy potential security weaknesses. For example, migrating major business systems like email and calendaring to Office 365 in the cloud may now take weeks and months rather than years.
The marketing and sale of solutions directly to business units and the bypassing of standard IT and security checkpoints, often referred to as “Shadow IT”, has also resulted in substantive blind spots for security teams that has hindered the ability of many organizations to maintain consistent alignment with security and compliance standards.
Third-Party Dependence Introduces New Business Risk Exposures
The healthcare industry has begun en masse to move critical business and clinical operations to the cloud including Electronic Health Records, finance and billing systems, and more. This means that information security risks for these business functions are becoming less focused on regulatory compliance and more driven by the availability and integrity of these essential systems used for the routine delivery of care.
As a result, third-party risk management programs have been vaulted from primarily compliance-driven functions to critical business-enabling functions that monitor and manage the organization’s vulnerable dependence on third parties to maintain patient safety and core business operations.
Meditology’s evaluation of vendors servicing healthcare demonstrates clearly that third parties are not consistently exercising the level of care and diligence necessary to deliver reliable care and uphold the regulatory requirements that Covered Entities are responsible for ensuring across their supply chain.
HIPAA & COVID-19 Updates and Enforcement Exceptions
OCR reported that no penalties will be applied for lacking a Business Associate Agreement (BAA) with video communications solutions used for telehealth during COVID-19 including Zoom, Apple FaceTime, Facebook messenger video chat, Google Hangouts, and Skype. Public-facing apps are still not permitted such as Facebook Live, Twitch, and TikTok.
Guidance was provided on existing disclosure provisions and amendments applicable to first responders. Disclosures to first responders are permitted so they can take extra precautions when dealing with COVID patients. However, Covered Entities are not permitted to post a list of infected patients internally or publicly and information may only be provided on a “per-call” basis.
No penalties will be applied for good faith sharing of PHI for public health including sharing from Business Associates. OCR noted that the Business Associate context was not made clear in prior rules and guidance. This includes COVID-testing sites in public locations like parking lots, etc.
OCR indicated that guidance on media and film crews has been re-issued from original 2016 date; the guidance reminds covered entities that you still can't release patient information, photos, or videos during COVID-19. This includes blurred images of patients which can still be identifiable (there was a specific case and issue with this scenario).
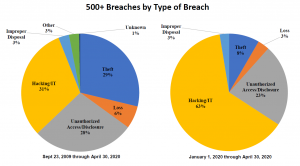
Trends from Reported Breaches
Let’s review the reported breach trends provided by OCR as we look back at 2019 and into the first half of 2020.
- 2019 was the biggest year of reported breaches of over 500 records to date, with 511 reported breaches in 2019 compared to 371 in 2018, 358 in 2017, 329 in 2016, and 270 in 2015.
- Hacking and IT/Network based incidents were identified as the largest growing source of beaches in 2020. This corresponds with other industry reports of massive increases in network and cloud-based attacks including a recent report from McAfee that cites a 630% increase in remote attacks on third party cloud services.[1]
- Email and phishing were identified as the most dominant attack vector for reported breaches in 2020.
HIPAA Compliance and Enforcement Actions and Trends
- Top sources of Covered Entity fines from OCR include Business Associate Agreements and inadequate Security Risk Analysis as top items on the list.
- OCR issued guidance in 2019 on the direct liability of Business Associates.[2] Business Associates must comply with the HIPAA Security Rule, must provide breach notification to Covered Entities and other Business Associates, and must cooperate with investigations from HHS and OCR.
- Security risk analysis activities by Covered Entities are too often lacking and not inclusive of third-party platforms and systems.
- Some Business Associates have taken a position that if they refuse to sign a Business Associate Agreement (BAA) then they are not liable for HIPAA Security Rule compliance mandates. OCR reiterated that the law specifies that organizations acting as Business Associates are in scope for HIPAA regardless of whether or not a formal BAA was executed.
- Breach reporting is taking longer, and rules are not being interpreted correctly by Covered Entities. For example, OCR indicated that you can’t wait for a full forensics investigation with your Business Associate or internal breach event in order to start the 60 day counter for notification. The 60-day mark starts as soon as you are aware of a potential breach. You must notify OCR “without reasonable delay”; 60 days is the maximum, and you should not wait that long every time out.
- There are still too many impermissible disclosures and a lack of appropriate safeguards for Covered Entities. OCR cited an example from Elite Dental which featured a patient complaint in a Yelp review for a dentist in Texas wherein the dental practice response included PHI, treatment, and payment details. Elite Dental was fine $10,000 for this impermissible disclosure.
- Several fines and enforcement activity resulted from lack-luster responses to security incidents by Covered Entities and Business Associates.
- OCR noted that fines and enforcement result from a variety of sources including complaints received (OCR receives ~28,000 complaints a year), compliance reviews (including reported breaches of 500+ records), and OCR-initiated investigations.
- In most cases, entities are able to demonstrate satisfactory compliance through voluntary cooperation and corrective action. Only 6 cases have resulted in Civil Monetary Penalties, while 69 have resulted in settlements and corrective action plans.
- OCR clarified that the OCR Security Risk Analysis tool provided on their website is designed for small organizations and provides a checklist of activities to conduct, which does not in itself satisfy the Risk Analysis requirement in the HIPAA Security Rule
Fines and resolution agreements last year that featured Business Associate compliance gaps include:
- West Georgia Ambulance ($65k) - OCR cited a lack of policies and procedures implemented to cover third party Business Associates.
- Bay Front Health ($85k) - citied with a lack of training and acknowledgement for the organization’s Business Associates and inadequate reporting of Business Associates who violate related policies and procedures.
- Dr Steven Porter ($100k) - fined in part for lacking executed Business Associate Agreements.
- Sentara Hospitals ($2.1m) - failed to execute a Business Associate Agreement with a sub-entity that experienced a breach event.
- Touchstone Medical Imaging ($3m) - OCR issued a resolution agreement with a requirement to revise and implement all policies and procedures for handling and maintaining Business Associate compliance and related agreements (BAAs).
Recurring HIPAA Compliance Issues
OCR noted recurring compliance issues including the following list. They also noted that the business continuity and disaster recovery gaps are increasingly identified as a result of reported ransomware breach events:
- Business Associate Agreements
- Risk Analysis
- Failure to Manage Identified Risk, e.g. Encryption
- Lack of Transmission Security
- Lack of Appropriate Auditing
- Patching of Software
- Insufficient Data Backup and Contingency Plan
- Individual Right to Access
OCR’s Recommendations for Best Practices
The following are OCR’s recommendations for best practices for Covered Entities and Business Associates’ compliance with HIPAA mandates:
- Review all vendor and contractor relationships to ensure BAAs are in place as appropriate and address breach/security incident obligations.
- Risk analysis and risk management should be integrated into business processes; conducted regularly and when new technologies and business operations are planned.
- Dispose of PHI on media and paper that has been identified for disposal in a timely manner.
- Incorporate lessons learned from incidents into the overall security management process.
- Provide training specific to organization and job responsibilities and on regular basis; reinforce workforce members’ critical role in protecting privacy and security.
- Review records access policies, procedures and practices.
- Train staff on the difference between Right of Access requests and authorizations.
Meditology’s Recommendations for Third-Party Vendor Compliance & Security Programs
- Develop repeatable, scalable, high-quality, and efficient vendor assessment models to keep pace with the rapid deployment of critical systems to cloud-hosted and downstream platforms.
- Invest in controls and business relationships to respond and recover from incidents involving third-party organizations and platforms.
- Incorporate third party vendor assessments into your HIPAA Security Rule risk analysis processes and reporting models.
- Inventory and prioritize cloud-hosted platforms for compliance and business criticality including patient care and operations (telehealth, EHRS, billing, etc.).
- Conduct targeted security assessments including penetration tests of critical and newly deployed cloud platforms including Office365, AWS, Azure, telehealth, and others. Attacks are ramping up and it is critical to identify any material exposures.
- Continue to require and pursue security certifications like SOC 2 and HITRUST for cloud-hosted solutions to obtain third party validation of controls.
- Build a cloud-specific security strategy; this may very well become the foundation of your overall enterprise security risk management program in the coming decade.
Conclusion
The future threat to healthcare information security and compliance will be less related to disclosure of sensitive patient information and more about patient safety, availability, and integrity of core business processes. Our team here at Meditology Services has the experience and capabilities to accelerate and position your information security risk and compliance programs to address the current and future protections required for securing the evolving healthcare delivery ecosystem.
Watch our webinar replay with OCR for more information and details on OCR’s 2019-2020 year in review.
[1] https://healthitsecurity.com/news/remote-attacks-on-cloud-service-targets-rose-630-amid-covid-19
[2] https://www.hhs.gov/hipaa/for-professionals/privacy/guidance/business-associates/factsheet/index.html