
BLOG
You Are Here. Mapping Out A Path to Security Program Maturity
Published On November 12, 2019
Blog Post by Brian Selfridge, ITRM Partner at Meditology Services
While many healthcare entities have addressed some fundamental information security capabilities, our industry is still regarded in many ways as lagging behind other industries that are popular targets of data predators. Healthcare CISOs are grappling with the next phase of security risk management: How to move from inception to growth, maturity and ultimately a robust, proactive security environment that can meaningfully address the complexity and dynamic nature of our industry.
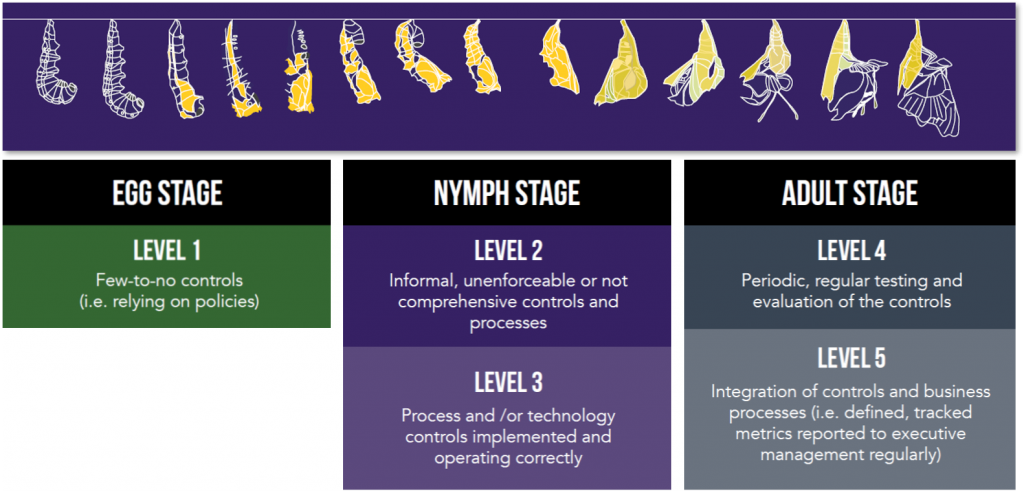
The challenge of data security maturity can be compared to the maturation cycles in the insect world. The Egg Stage is the inception stage for insects where they are just beginning life and rely on camouflage and hiding from predators as a primary defense. The next level of maturity are Nymphs (with a few more defense structures); and finally, some insects morph into the Adult stage where they reach their full potential in terms of adaptability and defenses.
The maturity of healthcare security programs can be viewed in a similar manner through three stages: Egg, Nymph and Adult. Let’s look at these briefly.
The Egg Stage – Focus on Compliance
In the Egg Stage, an insect is at inception and contained in a sac that protects it. For a healthcare data security program, the Egg Stage could be characterized as the inception point of assigning formal responsibility and oversight for the cybersecurity and compliance functions and addressing fundamental HIPAA compliance requirements.
Healthcare security programs in this early stage tend to be focused on compliance drivers including HIPAA, Meaningful Use, and MACRA obligations. The responsibilities for security program implementation are frequently decentralized and distributed across Information Technology and other departments. In the Egg Stage, security programs may have only basic security controls in place for a subset of key applications and infrastructure components.
Healthcare entities in this early stage often under-invest in information security protections for critical risk management areas like third party risk management, audit logging and monitoring, incident response, and enterprise-level risk analysis processes.
In presentations in 2019 at HIMSS and HIPAA Summit1, OCR representatives highlighted compliance trends that indicate that many healthcare entities remain in early stages of maturity. The OCR noted that breaches and hacking incidents are on the rise, however, many Covered Entities still lack effective Enterprise Risk Analysis and remediation tracking processes to identify and correct security weaknesses in their environments. The OCR representatives also noted a trend of ineffective inventory, tracking, and assessment of third-party Business Associates.
The Nymph Stage – Maturing, While Playing “Catch-Up”
In the Nymph Stage, insects develop a more sophisticated body and exoskeleton, but still do not reflect a fully developed Adult (with more defense features such as hardened skeletons and wings).
In healthcare, the Nymph Stage represents those organizations that have moved beyond purely compliance-focused programs and have begun to establish risk-based security models aligned with industry security standards like the NIST Cybersecurity Framework (NIST CsF) and the HITRUST Common Security Framework (HITRUST CSF).
Nymph-stage security programs often have dedicated, qualified security teams and some degree of security plans and procedures. Still, they often lack comprehensive controls and processes to protect data across the entire ecosystem both internally and externally. They often struggle with keeping track of data as it proliferates among internal business functions and hundreds of third-party business partners.
As a Nymph stage security program moves towards full maturity, the scope and scale of risk is better understood through the execution of enterprise-level risk assessments for any areas where sensitive information may reside. These middle-stage programs will take a multi-year outlook and have wide range corrective action and remediation plans. Investments and resources for security protections are also planned out in this stage.
But even with increased security controls, there often remain critical high-risk security and compliance exposures. Organizations in this stage are also continually playing “catch up” with known security control gaps and struggle to stay ahead of emerging threats and security control mechanisms.
The Adult Stage – Fully Mature & Taking Flight
For Adult insects, the survival rate by a predator attack is substantially improved by the physical and behavioral protections they have developed as adults. For example, caterpillars will have cocooned and emerged as beautiful and adaptable butterflies, which can fly away from most prey. Like a Monarch butterfly taking flight, a fully mature healthcare information security program is a beautiful thing to see fly.
In the Adult Stage, a healthcare security program is proactively managing risk. Adult-Stage organizations frequently measure and proactively manage risk through targeted and enterprise risk analyses, ethical hacking and technical penetration testing, and integration of security intro core business functions on a day-to-day basis. They adapt and learn from attacks and benchmark with peer organizations. Incident response plans are established, regularly communicated and tested. These response practices include targeted threat simulations including email and phishing-based attacks and response exercises.
An Adult-Stage security program is active in the acquisition and maintenance of information security certifications such as HITRUST CSF certification, NIST CsF certifications (available via the HITRUST Alliance), and SOC 2 Type 2 attestations. Security certifications reduce resource efforts needed to meet compliance requirements and communicate security standards to business partners and other stakeholders.
A key indicator of security program maturity is the ability of the organization to move beyond basic security controls adoption and compliance and into a model that supports effective risk-based decisions around security investments. Mature security programs are a vehicle for enabling the business, protecting patients and the company brand, and supporting effective enterprise risk management.
Where does your organization fall in the Maturity Cycle of Data Security Programs? Take a closer look at where you stand by downloading our white paper: 2019 | The Year of Metamorphosis for Healthcare Data Security.